This article leads you on the road to Linux security involving topics of SSH and MySQL. First, you could only hide ports, and create alias not easily guessed. Gradually, if theats still exist, you may add more methods, or even the strict IP whitelisting solution.
At the first place, we explain cause of dangers in worldwide webs with happened facts. Then depending on the selected security level, you should put effective decision on the websites. More secure methods always bring more inconvenience, but sometimes you must scarify somethings to rescue systems.
Estimated reading time: 7 minutes
EXPLORE THIS ARTICLE
TABLE OF CONTENTS
THE BASICS
HTTP & Other Attack
Let us begin with how the threats are produced, and then list what security weaknesses SSH and MySQL have. We also provide sample log data for evidence.
Trying to Guess Password
When a website is born, the founder has exposed it in a dangerous environment of worldwide Internet. Except if covering it with security plans, you can’t avoid threats like brute-force attack.
In cryptography, a brute-force attack consists of an attacker submitting many passwords or passphrases with the hope of eventually guessing correctly. The attacker systematically checks all possible passwords and passphrases until the correct one is found.
More seriously, once hackers guess the right password and come in, they may break your system or inject ransomwares into websites to ask you for ransom money.
SSH Threats
Considering the security weakness of Linux host services, SSH should be one of the candidates. SSH has a well-known port listening to not only remote users, but also unexpected stealth.
In Linux, the file /var/log/auth.log reveals attempting actions for both successful and failed authentications. Therefore, you can detect whether websites are under attack or not by just using shell command grep.
You may use grep "Failed Password" /var/log/auth.log to search for stealthy attempts as below.
Mar 21 19:40:20 hr1 sshd[9260]: Failed password for invalid user nagios from 123.13.221.191 port 44438 ssh2
Mar 21 19:43:16 hr1 sshd[9342]: Failed password for invalid user nagios from 123.13.221.191 port 44439 ssh2
Mar 21 19:46:13 hr1 sshd[9423]: Failed password for invalid user nagios from 123.13.221.191 port 44440 ssh2
Mar 21 19:49:15 hr1 sshd[9506]: Failed password for invalid user nesus from 123.13.221.191 port 44441 ssh2
Mar 21 19:52:05 hr1 sshd[9586]: Failed password for invalid user nexus from 123.13.221.191 port 44442 ssh2
MySQL Threats
MySQL has the default port 3306 for remote database access or client-server connections. If you are worry about that, you can close it by firewall. However, MySQL faces more security threats than SSH encounters, because phpmyadmin opens another gate that you have to protect, too.
From the file /var/log/apache2/access.log for Ubuntu (/var/log/httpd/access_log for CentOS), you will find that hackers are trying to guess password of MySQL user root through phpmyadmin. Such as the following log data, you can detect attacks by using grep pma_username.
140.143.167.250 - - [13/Mar/2020:11:47:54 +0800] "GET /phpmyadmin/index.php?pma_username=root&pma_password=000&server=1 HTTP/1.1" 200 11351 "-" "Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:52.0) Gecko/20100101 Firefox/52.0"
140.143.167.250 - - [13/Mar/2020:11:47:55 +0800] "GET /phpmyadmin/index.php?pma_username=root&pma_password=456&server=1 HTTP/1.1" 200 11350 "-" "Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:52.0) Gecko/20100101 Firefox/52.0"
140.143.167.250 - - [13/Mar/2020:11:47:56 +0800] "GET /phpmyadmin/index.php?pma_username=root&pma_password=root1&server=1 HTTP/1.1" 200 11350 "-" "Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:52.0) Gecko/20100101 Firefox/52.0"
140.143.167.250 - - [13/Mar/2020:11:48:34 +0800] "GET /phpmyadmin/index.php?pma_username=root&pma_password=root123456789&server=1 HTTP/1.1" 200 11351 "-" "Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:52.0) Gecko/20100101 Firefox/52.0"
140.143.167.250 - - [13/Mar/2020:11:49:06 +0800] "GET /phpmyadmin/index.php?pma_username=root&pma_password=p1O5oemS76C&server=1 HTTP/1.1" 200 11351 "-" "Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:52.0) Gecko/20100101 Firefox/52.0"
140.143.167.250 - - [13/Mar/2020:11:49:07 +0800] "GET /phpmyadmin/index.php?pma_username=root&pma_password=Abcd1234&server=1 HTTP/1.1" 200 11350 "-" "Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:52.0) Gecko/20100101 Firefox/52.0"
140.143.167.250 - - [13/Mar/2020:11:49:10 +0800] "GET /phpmyadmin/index.php?pma_username=root&pma_password=admin123456&server=1 HTTP/1.1" 200 11350 "-" "Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:52.0) Gecko/20100101 Firefox/52.0"
140.143.167.250 - - [13/Mar/2020:11:49:13 +0800] "GET /phpmyadmin/index.php?pma_username=root&pma_password=lenovo&server=1 HTTP/1.1" 200 11350 "-" "Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:52.0) Gecko/20100101 Firefox/52.0"
Dangerously, phpmyadmin allows hacking trials from worldwide threats. pma_username=root messages always appear in your log files everywhere unless preventing actions are taken. In the rest of this article, we will give you guidelines to follow up.
SECTION 1
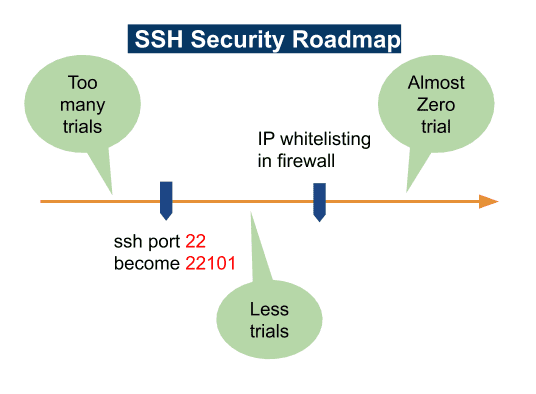
SSH Security Roadmap
For SSH security, the first step is to hide ports. Then we explain why inhibiting ssh root login is only a partial solution. Finally, we raise IP whitelisting as a robust approach.
1. Do Not Use Default SSH Port
The default ssh port is 22. You can change it to be 22101, for example. But Linux versions get distinct ways to do it, we pick some notes for you as below.
- For Ubuntu, update config file of /etc/ssh/sshd_config, and restart ssh service by sudo service sshd restart
- For CentOS, issue the command line of $semanage port -a -t ssh_port_t -p tcp 2244. As it is more complicated, you had better refer to the article about changing ssh ports for CentOS security to follow provided steps.
2. IP Whitelisting in Firewall
Unfortunately, changing ssh port only reduces the number of attacks, but does not inhibit them from happening. Many articles suggest stopping root login through ssh.
- Change /etc/ssh/sshd_config
- Let PermitRootLogin be no.
- restart sshd
However, this solution can not protect non-root users. Furthermore, it really results in discomfort feeling that root must move to the place where Console is located to login.
Our experiences prove that if limiting specified IP’s for ssh login, robust security should be effectively achieved. The solution is called IP Whitelisting. For example, you can list the dedicated IP’s for firewall as below. Thus incoming IP’s and ports are limited.
ufw allow from 71.208.162.101 to any port 22101
ufw allow from 71.208.162.102 to any port 22101
ufw allow from 71.208.162.103 to any port 22101
The default firewall configuration tool for Ubuntu is ufw, which is easy to use. We have found that after IP whitelisting, password guessings detected in /var/log/auth.log almost disappear.
SECTION 2
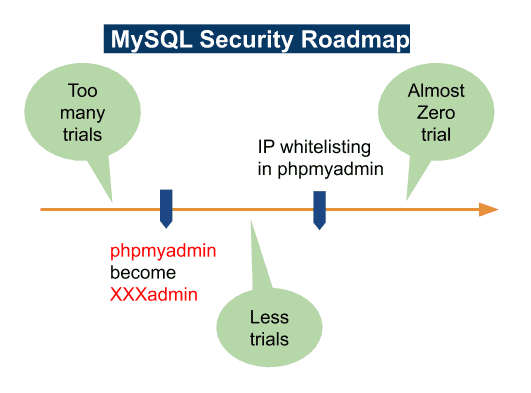
MySQL Security Roadmap
In this section, we focus on phpmyadmin for MySQL security. First, you can alter alias to hide phpmyadmin URL. Database is the most important. If ransomware seizes your data, you can not afford to take that risk.
Next, we suggest the complete solution of IP whitelisting in phpmyadmin. It did make MySQL very secure.
1. phpmyadmin Alias
As metioned in the last section, it is very important to protect phpmyadmin. Aliasing will be the first alternative because if you change /phpmyadmin to be /XXXadmin, the hacking attempt will get HTTP 404 NOT FOUND.
The following Apache access log indicates that phpmyadmin http requests are guessing MySQL root password.
140.143.167.250 - - [13/Mar/2020:11:47:54 +0800] "GET /phpmyadmin/index.php?pma_username=root&pma_password=000&server=1 HTTP/1.1" 200 11351 "-" "Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:52.0) Gecko/20100101 Firefox/52.0"
How to set aliasing? You can modify the first line of file /etc/apache2/conf-available/phpmyadmin.conf as below.
Alias /XXXadmin /usr/share/phpmyadmin
2. IP Whitelisting in phpmyadmin
If the above let you feel that websites are safe, you can stop here. Otherwise, there is more strict solution called IP whitelisting for phpmyadmin to use. In the file /etc/apache2/conf-available/phpmyadmin.conf, find the section of <Directory> and add settings as below.
<Directory /usr/share/phpmyadmin>
order deny,allow
deny from all
allow from 127.0.0.1
allow from 71.208.162.101
allow from 71.208.162.102
allow from 71.208.162.103
.....
Here shows the MySQL Security Roadmap.
FINAL
Conclusion
Every trial about SSH/MySQL security takes time to observe the effects, so the road could be longer than expected. We share our experience here to let you know that ip whitelisting did bring satisfying consequence to us.
Thank you for reading, and we have suggested more helpful articles here. If you want to share anything, please feel free to comment below. Good luck and happy coding!

Hey There. I found your blog using search. That is a well crafted really
article. I’ll make certain to bookmark it and get back to learning much more of your
useful information. Thanks for the post. I’ll be back :
)
Hope that helps you well. Thanks for your encouragement.